We live in a world of emerging technology, and with a rapidly evolving payments industry, the rise of real time payments, and an increasingly complex regulatory environment, one of the most significant technology challenges is security. To overcome security issues such as data breaches, ransomware attacks and hacking, enterprises are faced with the daunting task of keeping their own and their customers' data safe.
What is Point-to-Point Encryption?
Point-to-Point Encyption (PCI P2PE) is a standard established in July 2013 by the PCI Security Standards Council, a global forum formed by Visa, Mastercard, American Express, JCB, and Discover, for the ongoing development, enhancement, storage, dissemination, and implementation of security standards for account data protection. The aim of course is to provide access to a fail-safe payment security solution.
This can be a complex undertaking, as a point-to-point encryption solution is a combination of hardware, software, applications and processes that need to be audited and validated by the PCI Security Standards Council to assure that the payment data is secured.
Facts about security breaches
According to a white paper by Nuix called 'The Black Report', on average it takes hackers around 15 hours to breach an organization, locate critical value data and exfiltrate it. And on average, it takes an organization up to 300 days to discover it has been breached. The global average cost per data breach in 2020 was $3.86 million.
These costs include the disruption of business, lost sales, the arduous process of asset recovery, fines and compensation. There’s also non-monetary costs like brand erosion and reputational damage. With such dire consequences, it’s imperative that organizations make security a top priority. This is even more vital in the area of high value payments.
Average organizational cost to a business in the United States after a data breach from 2006 to 2020 (in million U.S. dollars)
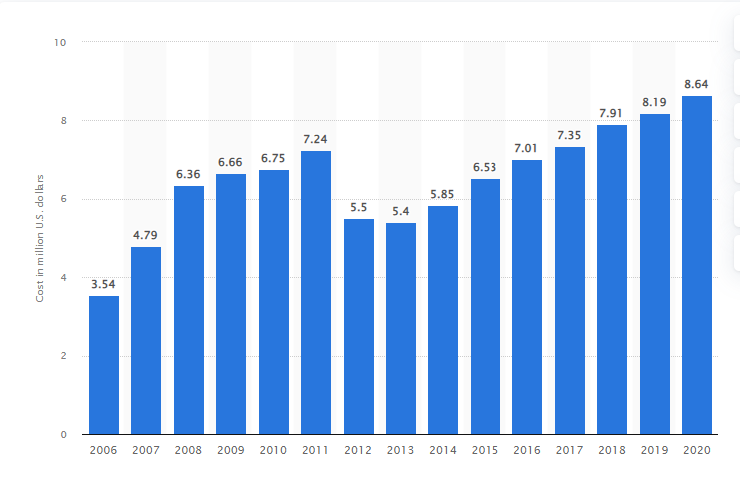
Image source: Statista
How does P2P encryption work?
Point-to-point encryption immediately converts confidential payment card data into indecipherable codes before payment processing. When the card is first used at the point of sale, the card data is securely transferred to the payment processor, where the encrypted codes are then decrypted and processed. This prevents hacking or fraud.
With point-to-point encryption, cardholder data is prevented from ever entering the point of sale environment. Point-to-point encryption significantly increases data security by protecting cardholder data 'in transit' and when it reaches its destination.
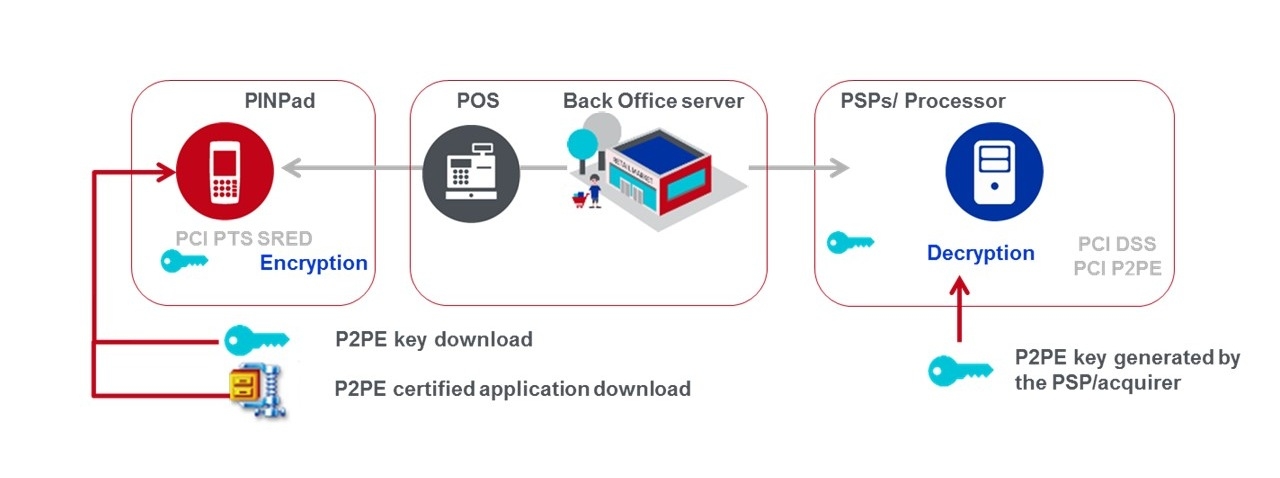
Image source: Ingenico
The main components of a P2PE solution are hardware, software and, most importantly the human facilitator of the Point-to-Point encryption solution.
Hardware
A Point of Interaction (POI), also known as a Point of Sale (POS), refers to the payment acceptance hardware used to capture card information. The device immediately encrypts data using a magnetic stripe or EMV chip or PIN card reader. All applications on the hardware device must also be compliant with point-to-point secure encryption standards.
Software
With regard to software, every P2PE solution contains encryption, decryption, application, and key management environments, configuration, design and other components. Point-to-point encryption software solutions can be Listed or Non-Listed according to the PCI Security Standards Council.
Facilitator
A third-party payment processor, payment gateway provider, acquirer or other third party that creates and implements encrypted data solutions to protect customer data during payment card transactions to reduce your risk of a data breach.
The encryption key and decryption key explained
Decryption and encryption keys are used to convert encoded/encrypted data into a form that is unreadable by a human or a computer, then convert it back to unencrypted data. Simply explained:
-
Encryption is a process of converting normal data into an unreadable form whereas Decryption is a method of converting the unreadable/coded data into its original form.
-
Encryption is done by the person who is sending the data to the destination, but the decryption is done by the person who is receiving the data.
-
The same algorithm with the same key is used for both the encryption-decryption processes.
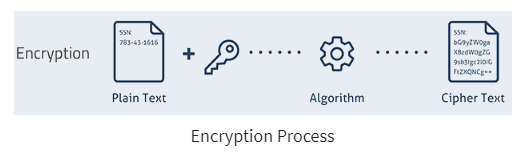
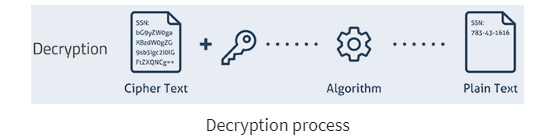
Images source: Guru99
Types of keys used in the encryption and decryption process
Symmetric Key:
A symmetric key uses the same string for both encryption and decryption, meaning that both the sender and receiver need the same key. This type of encryption, using a shared key is less secure. However, symmetric encryption works well for some tasks, such as file sharing between two computers.
Asymmetric Key:
With asymmetric encryption, the key is split in half to create a key pair consisting of a private key and a public key. A message is then encrypted with the public key, but it can only be decrypted with the corresponding private key. The receiver would first create an asymmetric key for themselves, then give out the public key to anyone they want to receive messages from but keep the matching private key.
End-to-End vs Point-to-Point encryption
The main difference between the two types of encryption is PCI validation. As mentioned, Point-to-point encryption is a standard established by the PCI Security Standards Council for payment card acceptance. Payment solutions that offer similar encryption but do not meet the P2Pe standard are referred to as end-to-end encryption (E2Ee) solutions.
P2PE
Point-to-point encryption directly links one system to another without the involvement of any other systems as it travels to the secure data zone of the payments processor. P2PE takes less time and adds greater security and confidentiality. A true P2PE solution is determined by three main factors:
-
The solution uses a hardware-to-hardware encryption and decryption process along with a POI device that has SRED (Secure Reading and Exchange of Data) listed as a function.
-
The solution has been validated to the PCI P2Pe Standard which includes specific POI device requirements and stringent controls regarding shipping and receiving at a merchant location, tamper-evident packaging, and installation.
-
A solution includes merchant education in the form of a P2PE Instruction Manual, which guides the merchant on POI device use, storage, return for repairs, and regular PCI reporting.
E2EE
An end-to-end encryption connection may indirectly link the point of payment card acceptance to the point of payment processing, but with multiple systems in between.
This increases hacker opportunities and may not meet the chain-of-custody requirements of P2PE. With an E2Ee solution, unencrypted card information can be easily read and stolen.
What should a PCI DSS validated P2PE solution include?
A PCI validated P2PE solution is required to have all of the following:
-
At the payment point of sale, payment card information must be safely encrypted.
-
P2PE approved applications must be used at the payment terminal (POI).
-
An encryption and decryption card reading device must be managed securely, and be part of a PCI-validated P2Pe solution that uses an algorithmic calculation to encrypt confidential payment card data.
-
Decryption media and all decrypted account information must be managed securely.
-
Encryption methodologies and cryptographic key operations, such as key generation, distribution, upload, and management, should be done securely.
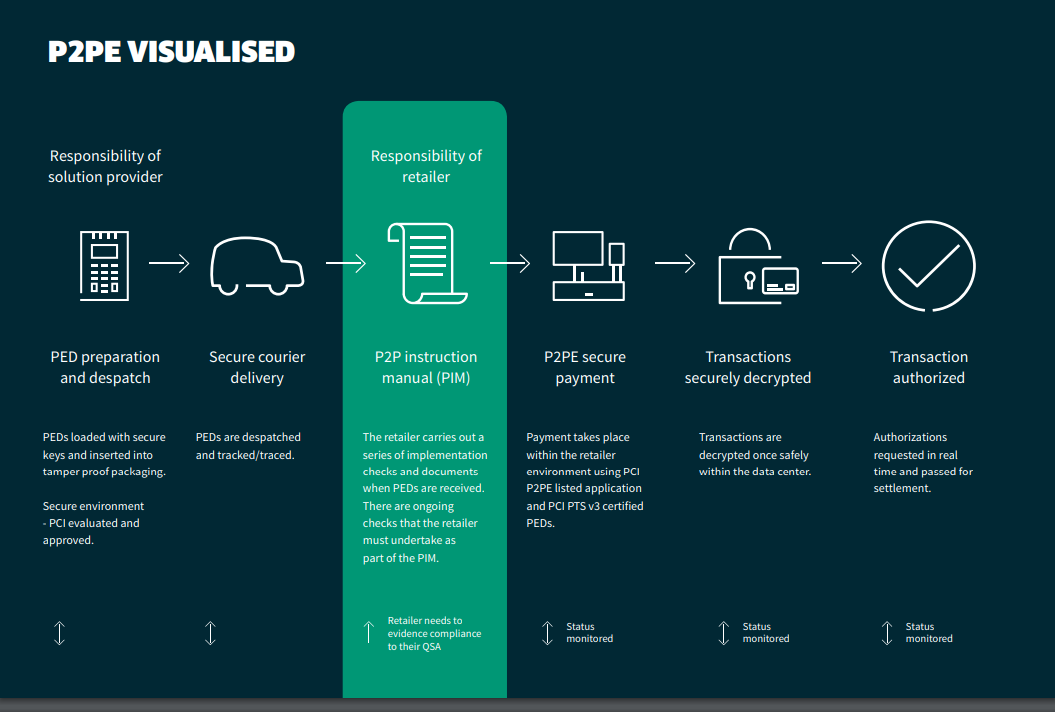
Image source: Fisglobal
What is tokenization?
Tokenization is a process by which sensitive information can be protected from others who do not have the proper authorization to view or manage it. The payments industry uses it to protect the Primary Account Number (PAN) of a card by replacing it with a unique string of characters.
While tokenization replaces sensitive data with a token, encryption encrypts or encodes the information so that it’s only hidden until the code is broken or decoded. The goal of this type of measure is aimed at making the information so well-hidden that it cannot be discovered.
The responsibilities of a P2PE solution provider
A P2PE solution provider is a third-party entity (i.e., a Processor, Acquirer, or Payment Gateway) that has overall responsibility for the design and implementation of a specific P2PE solution, as well as using strict controls to manage those solutions for its Merchant customers. The solution provider has overall responsibility for ensuring that all P2PE requirements are met, including any P2PE requirements performed by third-party organizations on behalf of the solution provider
Monitoring and managing your payment systems
With the growing complexity of the payments environment, it's vital that you can gain access to every component of your payment network and that sensitive data like a customer's card information is protected. Real-time transaction insights provide visibility and security controls within payment systems across the board.
For banks, central infrastructures and other key players in the real time payments space, transaction monitoring with IR Transact identifies glitches in payment systems and mitigates risk. It can also analyze historical information, spot abnormalities and fraud attempts.
The financial services industry deals with massive data volumes, so it's critical to detect complex patterns in real-time, correlate this information and analyze it quickly. Transact unlocks unparalleled insights into transactions and trends, streamlining the payments experience, from end-to-end.




